This year marks a significant change (improvement) on how Google I/O registration took place. Google originally announced a registration window in early April but was later clarified to be from April 15th to the 18th. Individuals wanting to register would enter into a lottery, which is scheduled to take place sometime today. The old system of ctrl + r or waiting for a spinner to ‘select an available ticket’ for you has been plagued with issues because of the large number of people wanting to register. In 2012 the registration process was completed within minutes.
In 2013 I managed to get a ticket three times but Google Wallet was having issues.
The first day of this years registration (Tuesday) I was away from my computer most of the day but I did manage to find time to register. After seeing the registration process, which was straight forward, I had wondered why Google had delayed the registration process for so long. In previous years the registration took place earlier in the year. If that is all they had planned it seemed odd that they would need to take the extra time that they did.
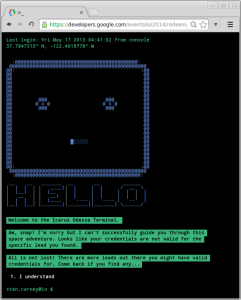
I didn’t get back in front of my computer until about 11PM that evening; and sure enough, there were some Google URL shortened links scattered around on Google Developers‘ website. Following the URL took you to an in-browser text-based game in which you appear to be piloting a space ship known as the Icarus Odessa.
If you followed an already claimed URL you would get a message stating your credentials were invalid but you were still allowed to continue with the game if you wanted to. A few steps into the game it mentions a code that gives you access to 37.7829° N, 122.4033° W, Earth, which happens to be the Moscone Center. Interesting… but it was late and I was tired.
Wednesday was also a very busy day for me but I had time in the morning to do some more digging. By this time all the initial plain text URL’s sprinkled throughout the Google Developers site, which were mostly contained to the Google Analytic’s pages, were returning the ‘Aw, snap!’ message, indicating somebody had already been there. The Google URL shortner provides basic statistics if you append .info to the end of the URL, allowing you to see when it was first accessed etc… I started plugging away to see if I could see a pattern of when the plain text URL’s were made available; I also started to think of where they might place the next batch of URL’s.
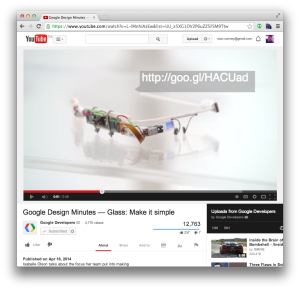
It didn’t take long before people started to post on Google+ about writing/using crawlers to search pages looking for goo.gl URLs. Around the same time a collection of new videos appeared on the Google Developers Youtube Channel. I watched the first video on design but had exhausted my available time to explore and had to move onto other things. 30 or so minutes later I had a small opportunity to dig around on my phone and sure enough there was mention in another Google+ post that the third video in the newly posted series contained an annotation with a now coveted goo.gl link to the Icarus Odesa! Crap…
My phone wouldn’t display the annotations on the video (starting at 0:46), like the screen capture shown above, but I was able to fumble around on my phone and pull out the annotations by manipulating the URL for this video:
into: https://www.youtube.com/annotations_invideo?video_id=L-lMnhiAzEw which displays all the relevant annotations. Note the <TEXT>http://goo.gl/HACUad</TEXT> in the XML.
Unfortunately, I was still a few hours away from being able to dedicate any block of time or effort to finding an unused link and things appeared to be escalating quickly. In a few hours, the links went from plain text present on a web page to embedded annotations in videos. Sure enough by the time I was able to check again (Wednesday evening) the bulk of new codes were showing up as ‘CAPTCHA’ styled text present in existing images on the Google Developer site.
By this time several HTTP crawlers had been created by individuals looking to secure a ticket to Google I/O ahead of today’s lottery. The crawlers used various tools and libraries to download images, web pages, and Youtube video annotations looking for more codes. My initial reaction was to stay away from automated crawlers; they require configuration, as well as some level of human intervention to inspect the images (where most of the codes seemed to be).
Instead, I resorted to several hours of pulling sitemaps and coming up with a proprietary system of scanning through images, which was 90% luck and 10% burning my eyes out of my head well into the evening. I was able to find two unused codes, I used one and sat back and watched how long it took for the other code to be used. My code was accessed 11 minutes after I used it, the other code took several hours before it was discovered.
Having already discovered a code, I didn’t pay much attention to any of the noise on Thursday; mostly people searching, asking for help, and begging for codes. I kept an eye on it throughout the day, but it wasn’t until somebody posted on the Google I/O community, about a string of text now appearing on the menu bar of the Google Developers Site, that I started to pay attention.
Base64 encoded SHA1 hash of a Google I/O registration URL. iEJ/aFz+jaDOaJon72bu4eL9FUc= rtxZRawESMtN4eLIyCnwg+bjaqE= EswtC4h5UKXQVcClfN/r3QfzS4A=
Reloading the page several times reveals there are actually three different values which happen to look like base64 encoded strings. Viewing the page source you see:
The thing to note is the CSS class s and the comment of ha! looks a lot like sha1. Maybe it was a Base64 encoded SHA1 hash?
I’ve been involved with Bitcoin for years and as a result I was in possession of several old GPU mining rigs that have since been re-purposed to mine Litecoin, Dogecoin and others. Unfortunately I didn’t have oclHashcat installed on either machine in order to attempt to crack the above Base64 encoded SHA1 hashes. This cost me somewhere between 30 minutes and 1 hour fighting with AMD Catalyst driver issues before I was able to successfully crack the three codes.
Initially I thought the driver issue was related to using the Netscape LDAP SHA hash type so when I originally tried to crack them I converted the decoded Base64 strings to hexidecimal first.
Appending .info to the three cracked goo.gl URL’s it turns out all three codes were already discovered and used by the time I noticed the Google+ post. Considering I already had a code, it was purely for fun anyway. I really do enjoy this type of thing.
Overall I think it was a definite improvement on the registration process and I’m looking forward to attending the conference! For those who did not find an unused code, good luck in today’s lottery!
Update: Even though the lottery for Google I/O tickets happened on Monday (April 21, 2014) Google was still planting new Icarus Odessa links as of Tuesday. See Blake Caldwell’s blog for more details.
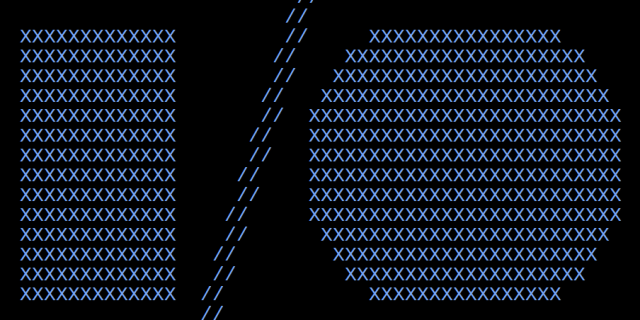

 I'm an idea developer. I'm also the Co-Founder, CTO of Redfall Technologies and Vogogo.com. I design and implement online payment systems, specifically online wallets, NACHA, Canadian Payments Association and credit card processing. I also dabble in all things technical.
I'm an idea developer. I'm also the Co-Founder, CTO of Redfall Technologies and Vogogo.com. I design and implement online payment systems, specifically online wallets, NACHA, Canadian Payments Association and credit card processing. I also dabble in all things technical.
A most excellent recount of the recent IO-14 challenge and adventure. The part where you re-purpose the bitcoin “mining-rigs” takes me back to teh classic tech movies of the 80’s…
Congrats! Please share a few thoughts later on your experience at the event!